I was in an exchange the other day with some folks talking about their perspective that all companies need to be using cloud computing. I agree, but my view is slightly different. My perspective is that depending on the company’s size, needs and applications they will likely continue to have in house systems. It’s not a choice between things, but a choice among things and an acceptance of the way things are and one answer doesn’t meet everyone’s needs. You can’t look at it as: clouds the answer, now what’s the question?
I was in an exchange the other day with some folks talking about their perspective that all companies need to be using cloud computing. I agree, but my view is slightly different. My perspective is that depending on the company’s size, needs and applications they will likely continue to have in house systems. It’s not a choice between things, but a choice among things and an acceptance of the way things are and one answer doesn’t meet everyone’s needs. You can’t look at it as: clouds the answer, now what’s the question?
Mobile computing is similar. It is the future interface of the enterprise, not really something special anymore. Embracing mobile devices and cloud computing will have a game changing effect, but it is not about the infrastructure but what we do with them and people want to do those things everywhere.
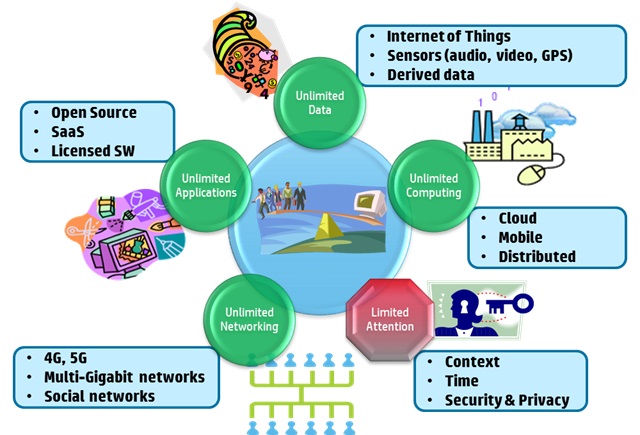
There are a number of other trends taking place like the IoT that are also shifting how organizations think about computing. It is interesting how this term is changing and how various organizations are trying to name it. It used to be ubiquitous computing, some call it ambient computing, but most still use the Internet of Things.
In any case the aggregation of sensors, devices, intelligence, and agents will shift how organizations generate value and shift IT to focus on systems of action.
Internet of Things Units Installed Base by Category (in Millions)
| Category | 2013 | 2014 | 2015 | 2020 |
| Automotive | 96.0 | 189.6 | 372.3 | 3,511.1 |
| Consumer | 1,842.1 | 2,244.5 | 2.874.9 | 13,172.5 |
| Generic Business | 395.2 | 479.4 | 623.9 | 5,158.6 |
| Vertical Business | 698.7 | 836.5 | 1,009.4 | 3,164.4 |
| Grand Total | 3,032.0 | 3,750.0 | 4,880.6 | 25,006.6 |
Source: Gartner (November 2014)
Many still look at these opportunities primarily from an infrastructure perspective, but I definitely do not. It is about the business and the hardware side is a small (but necessary) part. Organizations that will compete effectively in the coming years are going to shift their thinking to “and” and not “or” foundation. It is not all about IT, but IT has a role in enabling this flexibility.
By the way the output of the And not Or logic circuit illustration is always a one –> true.